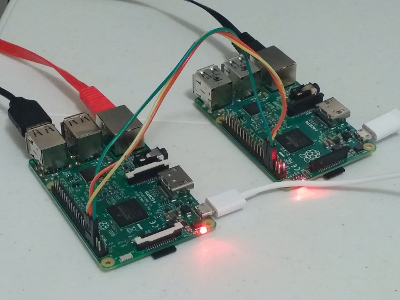
The same software that drives our flagship product, the PV-110 Hardware VPL, now runs natively on the Raspberry Pi 1, 2, and 3. Although not all of the original security features are available, this means you can run your own air-gapped dark intranet using off-the-shelf hardware. Here’s what you need:
- Two Raspberry Pi boards
- Three-wire ribbon cable
- SD/MicroSD cards with Prolaag Red & Black software installed
- MicroUSB power for each board
- An Ethernet cable for each board - one secure (LAN) and one public (WAN)
Can I wire two mixed & matched boards together?
Absolutely.
Which models are supported?
- Model B
- Model B+
- Pi 2 Model B
- Pi 3 Model B
Basically, if it’s a Pi with an Ethernet port, it’s supported.
Is a Pi assembly compatible with the PV-110?
100% compatible.
Is it capable of generating and using One Time Pad data?
Yes. The Pi assembly can use and charge USB storage devices for OTP content.
What does the Raspberry Pi version use for hardware entropy?
All Raspberry Pi models come with a built-in on-chip hardware random number generator (BCM 2835/2836/2837). We use that. Of course the assembly still makes hardware entropy available for auditing.
What’s the performance like?
Not as fast as the PV-110. The secure serial link between the boards caps VPL communications at 1mbps, and OTP charging rates run at about 40% of the hardware appliance. Web UI responsiveness is about the same.
I know the appliance uses 100% embedded software. Does the Raspberry Pi version use an OS?
Yes it does - a trimmed down version of the Linux kernel and an aggressively minified Busybox ecosystem (eg, a shell isn’t even installed). We use our own network stack for everything above the data-link layer.
I bought the programmed SD/MicroSD cards from Prolaag. Mind if I make back-up copies?
Absolutely not. Our software will always be DRM-free and we encourage you to make personal back-ups.
I’m a security researcher; what’s your position on reverse-engineering?
Go for it. We don’t prohibit reverse-engineering object code in our terms of service. If you think you’ve found a bug (good luck!), check to see if we’re offering a bug-bounty.
I’ve got an illegitimate copy of your software; what’s your recourse if I use it?
Of course we would prefer you buy legitimate copies of our software from us, but we will make no effort to detect or prevent this kind of infringement. Our product does not “phone home” and we do not include a single line of DRM code in this product. Safety and privacy are our priority, not lawsuits.
That said, we make no assurances about the integrity of illicit copies of our software. If confidentiality is important to you, buying legitimate, unmolested software from us is the safer option.
