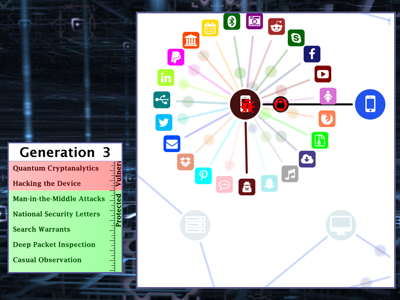
A brief history of secure communications on the Internet.
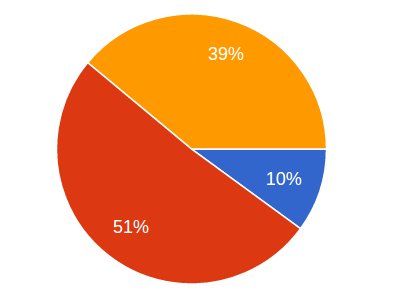
Read MoreHere's what people think about whether unbreakable encryption should be available to everyone.
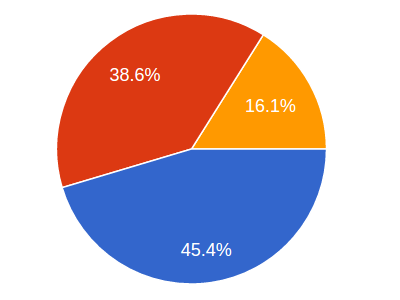
Read MoreWe went to the public and asked if such a thing as unbreakable encryption existed. Here are the results.
Read MoreVideo describing the scientific approach used to verify hardware randomness, and providing live comparisons to common alternatives.
Read MoreTime-lapse recording of the soldering and final assembly of the Prolaag Hardware VPL, from base components to the strongest digital privacy appliance available in 87.5 seconds.
Read MoreThe same software that drives our flagship product, the PV-110 Hardware VPL, now runs natively on the Raspberry Pi 1, 2, and 3.
Read MoreCheck out a few of the reasons we believe Prolaag has the most secure VPN available.
Read MoreRead how we make it easy to do independent verification of the entropy we produce.
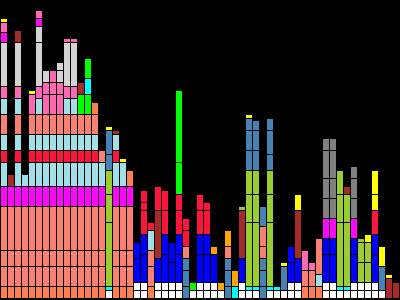
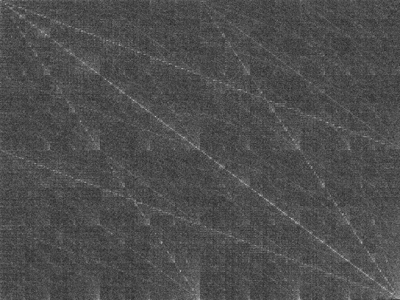
Read MoreHow our open source graphical inspection tool helps us measure randomness.
Read More